Advanced data protection for sensitive and unstructured
information
Confidencial secures the sensitive, unstructured data that fuels your business like IP, PII, or PHI, wherever it lives or moves. We extend Zero Trust to the data itself, giving enterprises and regulated industries visibility, control, and protection across clouds, third parties, and AI.
Confidencial is built on patented, award-winning technology developed by SRI for Defense Advanced Research Projects Agency (DARPA). Built for regulated industries. Trusted by leaders in healthcare, finance, and government.
Selective encryption for unstructured data
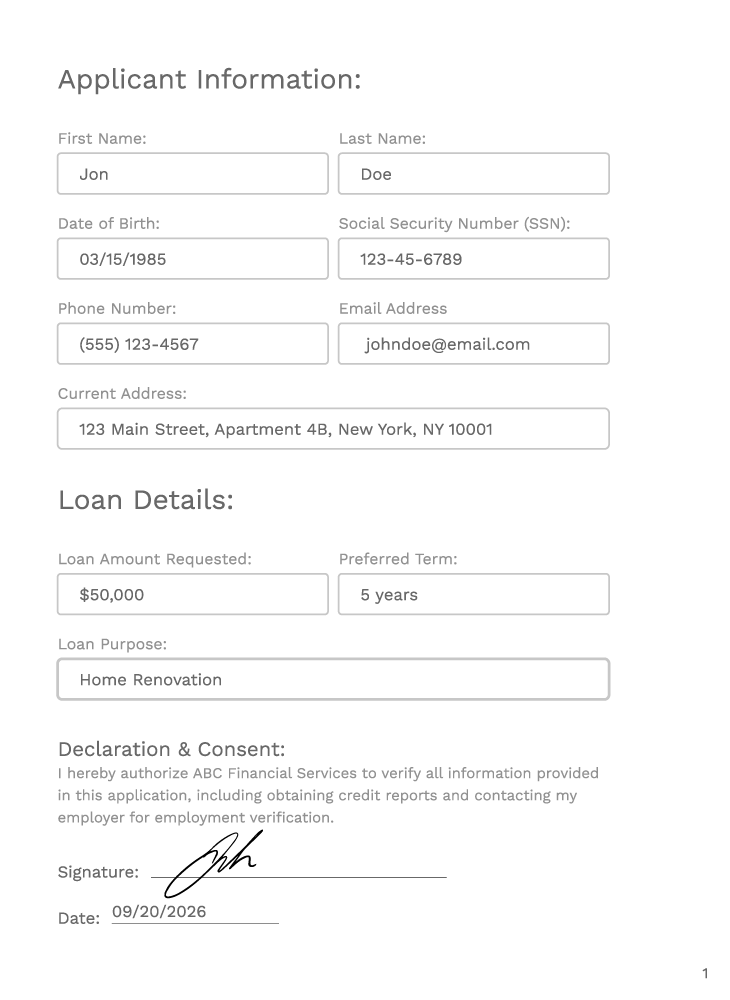
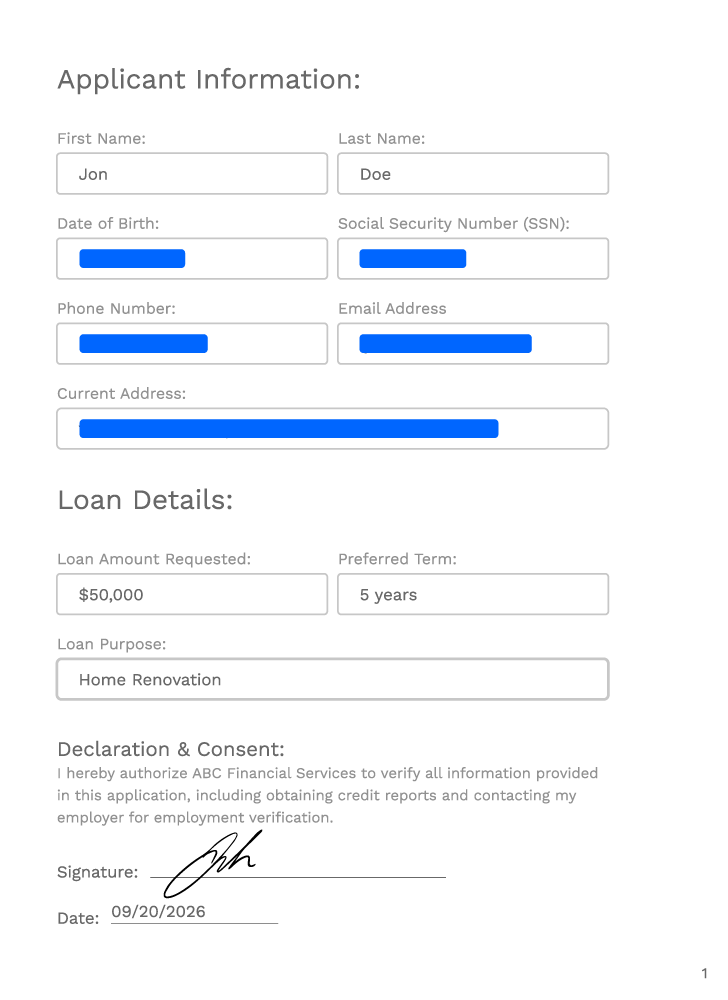
Our patented selective encryption is like using a scalpel instead of a hammer for data protection, encrypting only the sensitive parts of a document —down to the word, paragraph, cell, or pixel —while leaving non-sensitive information accessible. The protection is embedded into the metadata and travels with the document, even if it is shared beyond your network or used/sent by AI agents.
Before
After
What Confidencial protects and enables
Drive smarter AI with safer data
You can now safely harness all of your enterprise documents without compromising security.
Scan, classify, and secure sensitive data with context-preserving tokenization—or use selective encryption for stronger protection that locks critical data down while AI workflows and pipelines run smoothly thanks to automated safeguards that keep you in control.
Strengthen your security posture
Sensitive data is everywhere, but most organizations don’t see the risks in time.
Confidencial uncovers hidden data threats before exposure, quantifies financial risk from potential breaches, and prevents unauthorized access or use. Reducing attack surfaces across hybrid, cloud, and on-prem environments protects your sensitive information without disrupting workflows.
Make compliance easier
Managing data security and compliance shouldn’t be a headache.
Confidencial simplifies classification and policy enforcement, automates compliance with built-in security controls, and reduces audit burdens with continuous monitoring and reporting that keeps you fully compliant and aligned with Executive Order 14117, NIST AI, and Cybersecurity frameworks.



Secure the way you share, request, and sign
Sharing sensitive data doesn't have to mean sacrificing security.
Confidencial lets you securely request and send documents, collaborate externally, and collect e-signatures, while keeping full control with encryption, watermarking, and access tracing baked in. Zero trust, built-in.
One platform for many teams
Stop choosing between data protection and data productivity. Confidencial gives organizations a no-compromise path to security and compliant AI readiness.
Security Leaders & Teams
Know where your sensitive data is—and protect it.
—
—
—
—
—
Continuously discover exposed sensitive content across cloud and on-prem.
Use granular encryption down to the word, image, or field.
Build Zero-Trust that travels with the data, not just around it.
Secure document sharing and eSign without opening new threat surfaces.
Enable collaboration without compromising control.
GRC, Legal & Privacy Teams
Achieve compliance and enable secure legal workflows.
—
—
—
—
—
Classify and protect PII, IP, and regulated data automatically.
Enforce policy-based protections for shared and signed documents.
Ensure audit-ready encryption for contracts, legal memos, and filings.
Maintain defensibility with traceable eSign actions and sharing logs.
Prove compliance with real-time visibility and reporting.
AI Leaders & CEOs
Turn sensitive data into a strategic advantage.
—
—
—
—
—
Empower GenAI and agentic AI without exposing what’s sensitive.
Use protected datasets for analysis, modeling, and insights.
Enable governed sharing across partners, teams, and LLM workflows.
Ensure privacy and utility with context-preserving protection.
Monetize data responsibly without compliance risk.
Robust out-of-the-box capabilities
IDP Integrations: Microsoft Entra, Okta, Ping
Hybrid and multicloud-ready
Supported policy suites: PII, PCI, HIPAA, GDPR
Supported sources: OneDrive, Amazon S3, Azure Blob, Google Drive, Box, on-prem servers
Supported file formats: PDF, Word, Text & Image Files, Excel, PowerPoint
Encrypted storage of backend keys & seamless path to PQC
Secure by design, private by principle
Built with a security-first design, our zero-trust platform ensures your data stays yours—we can’t see, store, or access it.
ISO/IEC 27001:2022 Certified
HIPAA Compliant
PCI-DSS Compliant
SOC 2 Type 2 Certified
Mission-driven from the start
Confidencial was born from DARPA-funded research at SRI, built by a team of cybersecurity engineers and PhDs on a mission to safely unlock the massive potential of GenAI. Our technology was originally developed to meet the military’s need for protecting sensitive and proprietary data.
Since our start, Confidencial was built for two core objectives: enabling secure, privacy-preserving data sharing and ensuring resilience against large-scale compromise. Now, we’re bringing that same battle-tested security and control to organizations that need AI to work smarter and without the risk. No compromise, just control.
Get started with a comprehensive risk assessment
Unknowns in your data landscape can drive costly risks. Our advanced risk assessment keeps you ahead of the problem by uncovering unstructured data you didn’t even know you had. Get a detailed report with actionable insights into sensitive data exposures, compliance gaps, and potential vulnerabilities.
There’s a lot of value waiting in your data – Confidencial can help you get there.
Start your data protection journey on solid ground.